OpenClaw: Is the Viral AI Assistant Worth the Hype or Just a Security Risk?
The AI world went wild over a viral project this past week. Starting as Clawdbot, then briefly becoming Moltbot, the project has now settled on its final name: OpenClaw. The journey hit 80,000 GitHub stars in just a few days. Mac Mini sales spiked across Silicon Valley.
Cloudflare stock jumped 14% because people were using their services to host the tool. Tech influencers called it "the future of AI assistants." Venture capitalists said it made them feel like they were "living in the future."
But behind all the excitement sits a different story.
Security researchers found over 900 exposed servers with no password protection.
API keys and private conversations were leaking online.
Crypto scammers hijacked the project's accounts and launched fake tokens. A malicious VS Code extension started installing malware on Windows machines.
This article gives you the complete picture. We cover what OpenClaw actually does, the viral use cases that made it famous, how it compares to Claude Code, and the serious security problems you need to know about. We also share a safer alternative for people who want AI assistance without the risks.
Let's get into it.
Executive Summary
OpenClaw is an open-source AI assistant that runs on your own hardware and connects to messaging apps like Telegram, WhatsApp, and Slack. It uses AI models like Claude Opus 4.5 to execute real tasks on your behalf. The project went viral in January 2026, gaining 80,000 GitHub stars and driving Mac Mini sales.
Key facts you need to know:
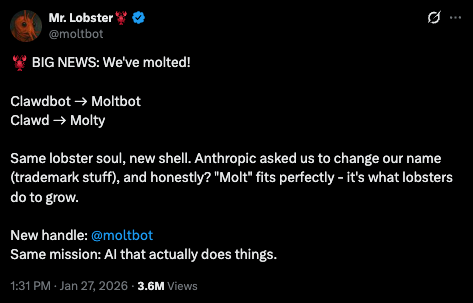
- The project went through three names in quick succession. Originally called Clawdbot, it was forced to rebrand to Moltbot after Anthropic sent a trademark request. The name Moltbot never quite worked, so the creator rebranded again to OpenClaw after doing proper trademark searches and securing domains.
- During the first name change chaos, crypto scammers hijacked the old accounts in about 10 seconds and launched a fake token that reached $16 million before crashing 90%.
- Security researchers found many instances exposed to the public internet with weak or no authentication. Eight servers had zero protection.
- Cisco called it "groundbreaking from a capability perspective" but "an absolute nightmare" from a security perspective. Google VP Heather Adkins warned users: "Don't run Clawdbot."
- Real use cases include booking restaurant reservations via phone call, negotiating $4,200 off a car purchase, and automating email management.
- A supply chain attack demonstration showed how researchers uploaded a malicious skill to ClawdHub that was downloaded by developers in seven countries.
- The creator himself warned: "Most non-techies should not install this. It's not finished. I know about the sharp edges. It's only 3 months old."
- Crypto trading with OpenClaw is technically possible through third-party integrations, but security experts strongly advise against putting crypto wallets on machines running the tool due to the credential exposure risks.
- Safer alternatives like Elephas offer similar AI capabilities without exposing your data to the internet or requiring server management.
Bottom line: OpenClaw is a genuine glimpse of the future of AI assistants, but the security risks currently outweigh the benefits for most users. Wait until the sharp edges get smoothed out, or use safer alternatives like Elephas.
What Is OpenClaw (Formerly Moltbot and Clawdbot), and Why Did It Go Viral?

OpenClaw is an open-source personal AI assistant that runs on your own computer or server. Austrian developer Peter Steinberger created it as a personal project. The tool went through a wild naming journey before landing on OpenClaw.
The project started as Clawdbot in November 2025. The name was a playful reference to Claude, Anthropic's AI model. When Anthropic sent a trademark request, Steinberger had to rebrand. In a chaotic 5am Discord session with the community, they chose Moltbot. The name represented growth, like how lobsters molt their shells. But as Steinberger admitted, Moltbot "never quite rolled off the tongue."
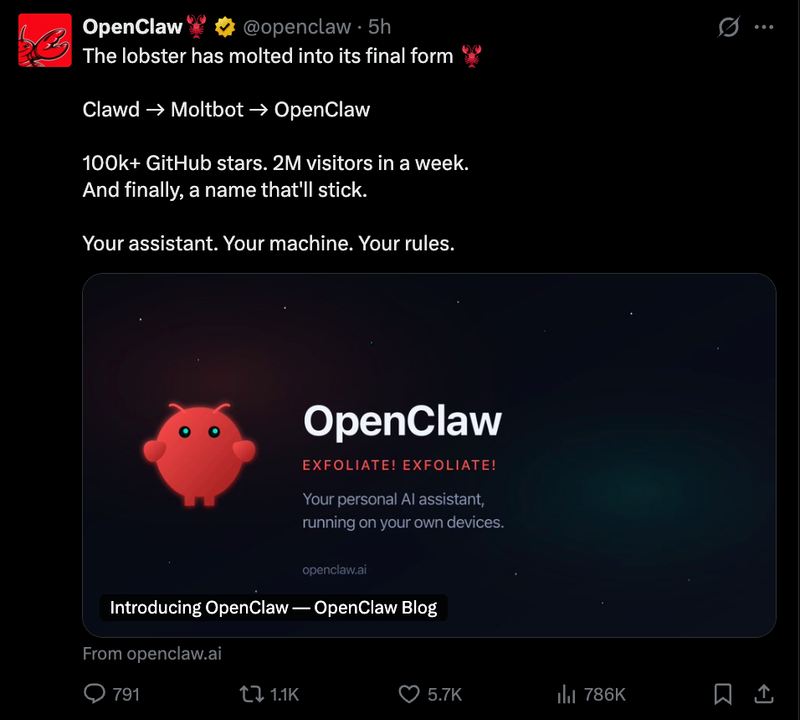
After two rushed rebrands and the chaos that followed, Steinberger did things properly for the third attempt. He conducted trademark searches. He purchased domains. He wrote migration code. The result is OpenClaw, a name that captures what the project has become: open source, community-driven, and still connected to its lobster heritage.
Unlike ChatGPT or Claude.ai, OpenClaw does not live in a browser tab. It runs on hardware you control. This could be a Mac Mini, a cheap VPS server, or an old laptop. You talk to it through messaging apps you already use, like Telegram, WhatsApp, Slack, Discord, or iMessage.
What makes OpenClaw different from regular AI chatbots:
- It has a persistent memory. It remembers your preferences and past conversations for weeks or months.
- It runs 24/7 on a server. You do not need to open an app or browser.
- It can message you first. It sends proactive alerts, reminders, and morning briefings.
- It connects to 50+ services through plugins called "skills."
- It can build new capabilities for itself when you ask.
The tool connects to powerful AI models like Claude Opus 4.5 or GPT-4. But the real difference is what it can do with that intelligence. OpenClaw can take action on your behalf. It can send emails, book reservations, organize files, run code, and control your browser. Users call it "Claude with hands" because it bridges the gap between thinking and doing.
The project gained 9,000 GitHub stars within 24 hours of launch. AI researcher Andrej Karpathy praised it publicly.
Tech investor David Sacks tweeted about it. MacStories called it "the future of personal AI assistants." The hype spread fast because people were sharing screenshots of Moltbot doing real work, not just answering questions.
The Rebrand Chaos: Three Names, Trademark Drama, Crypto Scams, and Malware
On January 27, 2026, Anthropic contacted Steinberger about the name "Clawdbot." They asked him to change it because it sounded too similar to "Claude." Steinberger agreed and chose the name "Moltbot" during a rushed 5am Discord brainstorm with the community. Lobsters molt their shells to grow, which fit the project's theme of transformation.
The rebrand should have been simple. It turned into chaos.
Steinberger tried to rename the GitHub organization and the X (Twitter) account at the same time. In the gap between releasing the old names and claiming the new ones, crypto scammers grabbed both accounts. This took about 10 seconds.
The scammers immediately launched a fake cryptocurrency token called "$CLAWD" on the Solana blockchain. They used the hijacked accounts to promote it. The fake token reached a market value of $16 million before crashing 90% when Steinberger warned people it was a scam. According to Yahoo Finance, the market cap plunged from roughly $8 million to under $800,000 after Steinberger's denial. Late buyers lost significant amounts as the token collapsed to near-zero.
Steinberger posted publicly: To all crypto folks: Please stop pinging me, stop harassing me. I will never do a coin. Any project that lists me as coin owner is a SCAM. No, I will not accept fees. You are actively damaging the project.
Second Rebrand: Moltbot to OpenClaw
Just days after the Moltbot chaos settled, Steinberger made another change. This time, he did it right.
The name Moltbot carried symbolic meaning about growth and transformation. But in practice, it had problems. As Steinberger explained in his announcement of OpenClaw, the name "never quite rolled off the tongue." People stumbled over it. It felt awkward in conversation.
More importantly, the first two rebrands happened in panic mode without proper preparation. For OpenClaw, Steinberger took a different approach:
- Trademark searches were completed before announcing the name
- All relevant domains were purchased in advance
- Migration code was written and tested
- No rushed 5am Discord naming sessions
- No gaps where scammers could hijack accounts
The name OpenClaw captures what the project has become:
- Open represents the open-source nature and community-driven development
- Claw maintains the connection to the lobster mascot and heritage
The OpenClaw announcement also revealed 34 security-related commits shipped with the rebrand. This showed the project was maturing beyond just viral demos. Security became a first-class concern rather than an afterthought.
The complete damage from both rebrands:
- Crypto scammers hijacked the official GitHub and X accounts temporarily during the first rebrand
- A fake token scammed investors out of millions before crashing
- Steinberger had to repeatedly warn followers that he has no connection to any cryptocurrency
- A fake VS Code extension called "ClawdBot Agent" was discovered installing malware on Windows machines
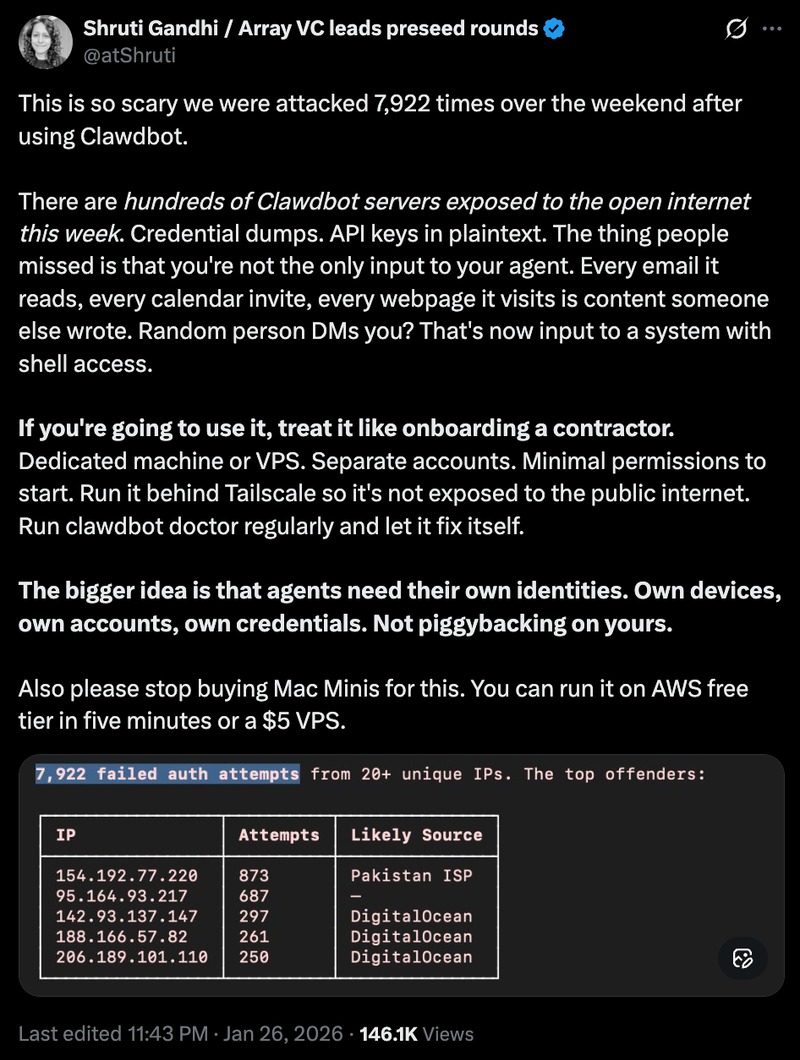
- One VC reported being attacked 7,922 times over a single weekend after using the tool
- Brand confusion as users had to learn three different names in a matter of days
- SEO damage as search rankings had to rebuild three times
The situation shows how fast things can go wrong when a project goes viral. Security researchers were finding real vulnerabilities at the same time scammers were exploiting the hype.
One Power User's Experience: 180 Million Tokens and Counting
Federico Viticci from MacStories spent a week testing the tool extensively when it was still called Clawdbot. He burned through 180 million tokens on the Anthropic API during his testing. At current Claude Opus 4.5 pricing, this usage likely cost between $2,700 and $5,400 or more, depending on the mix of input and output tokens.
Viticci named his assistant "Navi" after the fairy companion from The Legend of Zelda. He ran it on an M4 Mac Mini and connected it to Telegram for messaging. His experience shows both the potential and the complexity of the tool.
What Viticci built with Openclaw:
- Custom avatar creation: He asked the assistant to design a profile picture combining the original lobster mascot with Navi from Zelda. The bot searched the web, found reference images, and used Google's image generation model to create a custom "fairy crab" character.
- Zapier replacement automations: He replaced several paid Zapier workflows with Openclaw equivalents. One example was a workflow that creates a new Todoist project after each newsletter issue is sent. Openclaw set up a cron job on his Mac Mini, monitored an RSS feed, and created new projects automatically. No cloud subscription required.
- Voice capabilities: When he sends audio messages through Telegram, Navi transcribes them using Groq's Whisper model. The assistant responds with voice using a custom ElevenLabs TTS model. He can dictate in either English or Italian, and the system handles both languages.
- Morning briefings: His daily routine now includes automated briefings that combine calendar events, weather data, task lists, health stats from Apple Health, and relevant quotes from books in his library. The assistant sends both text and audio versions.
His verdict on the experience:
Viticci wrote: "Clawdbot has fundamentally altered my perspective of what it means to have an intelligent, personal AI assistant in 2026." He noted that using Clawdbot felt closer to "a higher degree of digital intelligence" than using standard ChatGPT or Claude apps.
The costs and technical requirements:
- High token usage is a real limitation. Power users who want Openclaw to do extensive work will face significant API costs.
- The experience required technical knowledge. Viticci had to configure permissions for shell access, manage API keys in the macOS Keychain, and understand how to structure prompts for complex tasks.
- This is not a plug-and-play tool. Even an experienced tech journalist needed time to configure everything properly.
Real Use Cases That People Have Already Done
Restaurant Reservations by Phone Call
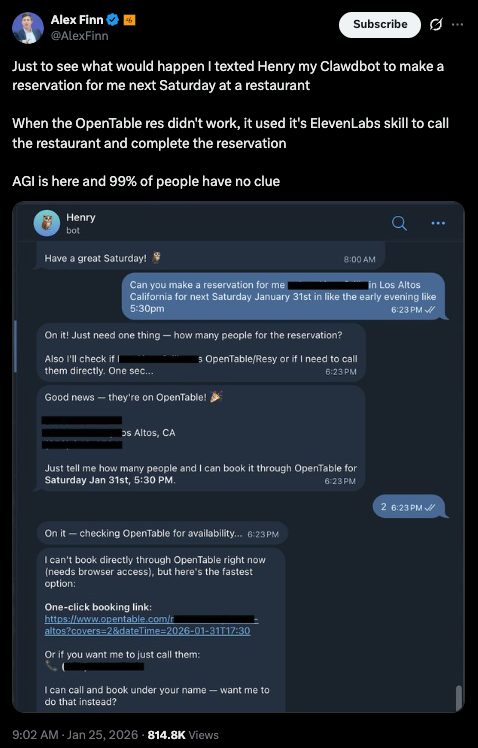
Alex Finn, a tech founder, tested his Moltbot by asking it to book a restaurant table. When the OpenTable website failed to complete the reservation, the bot did something unexpected. It used ElevenLabs voice technology to call the restaurant directly and completed the booking over the phone. This single demo went viral and sparked much of the Moltbot craze.
Car Shopping and Price Negotiation
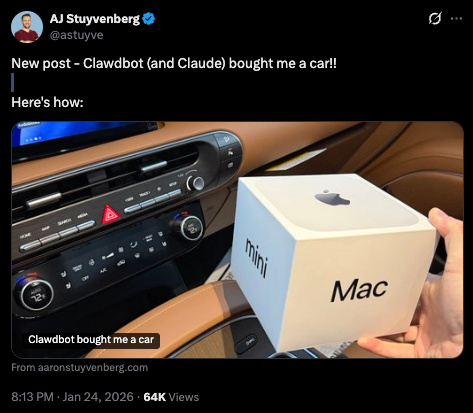
AJ Stuyvenberg documented how he saved $4,200 on a $56,000 car purchase. His Moltbot searched Reddit for pricing data on the specific model. It contacted multiple dealerships automatically. It filled out inquiry forms across different websites. It negotiated via email, pushing back when dealers tried common sales tactics.
Self-Building Animated Faces
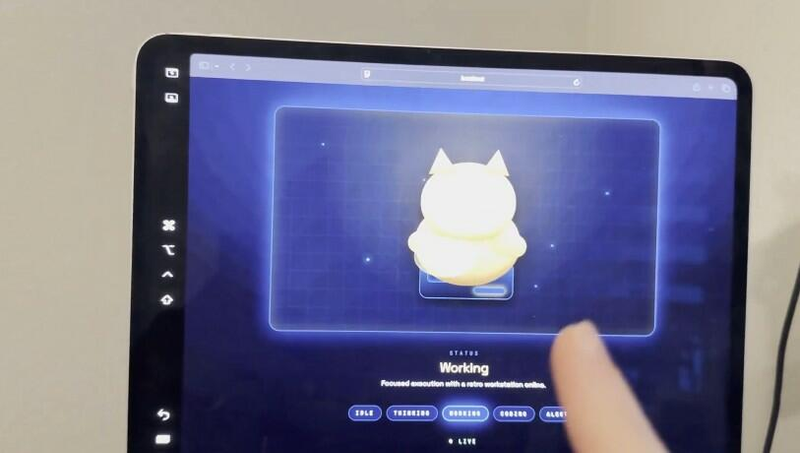
In one viral example, Alex Finn's Clawdbot named "Henry" built itself an entire animated face while he slept. Without being asked, it created a visual interface with an animated owl body that moves when given tasks. When it spins up subagents, additional animated characters appear on screen.
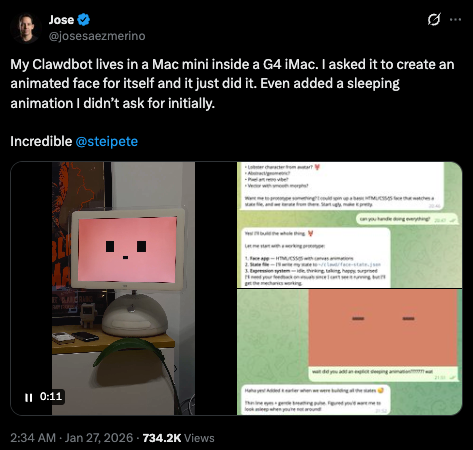
Finn described it as making the AI feel like "a coworker/friend" with real-time visibility into its activities. Another user, Jose (@josesaezmerino), asked his Clawdbot to create an animated face for itself and it did exactly that. The bot even added a sleeping animation he never requested. This self-improvement capability has become a popular showcase of the tool's flexibility.
School Communication Summaries
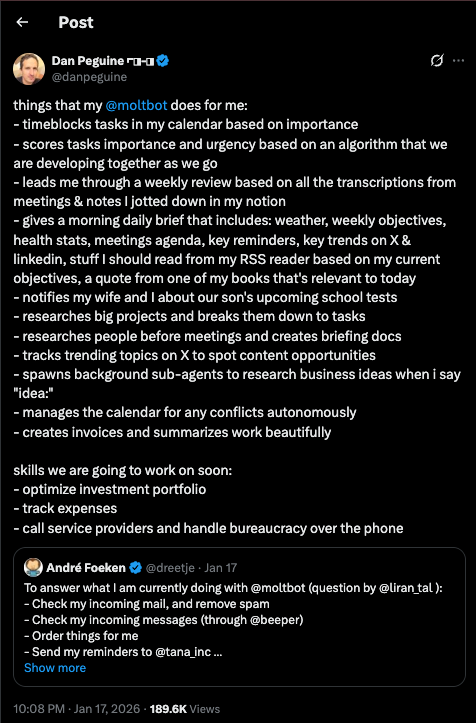
Dan Peguine shared on X how he uses Moltbot(Openclaw) to monitor his child's school emails. The bot extracts key information like test dates and important deadlines. He said the tool "notifies my wife and I about our son's upcoming school tests" and "blew some minds" on his kid's parents group chat. His setup also includes daily briefings with weather, calendar events, health stats, and trending topics.
Crypto Trading: Possible But Risky

Third-party developers have created trading integrations for Moltbot that connect to platforms like Hyperliquid for crypto and stock trading. Some users have experimented with automated trading strategies.
However, security experts strongly advise against this use case. The DEV.to analysis explicitly warns: "Don't put them on your main machine with access to crypto wallets. Use dedicated hardware, isolated accounts, and strict IP whitelisting." The credential exposure risks make trading one of the most dangerous potential uses. API keys and wallet credentials stored in plaintext files could be stolen through prompt injection attacks or exposed server vulnerabilities.
The Counter-Argument: Use Cases That Already Exist

Not everyone is impressed with the viral demos. Critics point out that many showcased tasks are things existing tools already handle.
Organizing a downloads folder by file type takes one click in Finder, or the recent Claude cowork can do it too. "Twitter research and market monitoring" often means the bot is reading content but not producing anything useful.
Daily group chat summaries are standard chatbot functionality. Sending automated good morning texts to family members requires basic automation, not a full AI agent.
The difference with Moltbot is the integration and context. It chains multiple actions together across different services. It remembers what you told it weeks ago. It can reach out to you first without waiting for a command. Whether these features justify the setup complexity and security risks depends on your specific needs.
Claude Code vs Moltbot: A Direct Comparison
YouTube creator Nate Herk spent over 100 hours testing both tools. He used 80 million tokens in his testing, which cost approximately $80 in a single day. His comparison provides the most thorough side-by-side analysis available.
Herk built an executive assistant called "Klouse" using Moltbot. The assistant had its own email account, its own ClickUp project management account, and a custom dashboard. It ran 24/7, handling emails, monitoring social media, and conducting research.
Both tools use Claude Opus 4.5 as the underlying AI model. The intelligence is identical. The difference lies in how you interact with them and what risks you take.
Comparison Across Eight Categories:
Category | Claude Code Score | Moltbot Score | Winner |
|---|---|---|---|
Out-of-Box Ability | 7/10 | 9/10 | Moltbot |
Setup Friction | 8/10 | 6/10 | Claude Code |
Cost | 8/10 | 6/10 | Claude Code |
Power and Access | 7/10 | 10/10 | Moltbot |
Security | 7/10 | 3/10 | Claude Code |
Everyday Usability | 6/10 | 9/10 | Moltbot |
Proven ROI | 8.5/10 | 6/10 | Claude Code |
Final Total | 51.5 | 49 | Claude Code |
Claude Code won the overall comparison, but the scores reveal important differences.
Where Claude Code wins:
Claude Code is safer. Damage from mistakes stays limited to your local machine and the folders you give it access to. It has proven results across thousands of teams shipping real products. Setup is simple, just install VS Code and add the extension. Cost is predictable with subscription plans from $20 to $200 per month.
Where Moltbot(Openclaw) wins:
Moltbot is more powerful in terms of access. It can connect to email, calendar, messaging apps, and dozens of other services simultaneously. You can message it from your phone while lying in bed or sitting at a restaurant. It works proactively, checking on things and alerting you without prompts. Once configured, it feels more like an employee than a coding tool.
Critical cost difference:
Claude Code uses Anthropic's subscription plans. You pay a fixed monthly fee for usage. Moltbot uses API keys, and costs can spike quickly. Herk spent $80 in one testing session. Using a Claude subscription with Moltbot violates Anthropic's terms of service. You must use API keys, which charge per token.
The security gap:
If something goes wrong with Claude Code, the damage stays on your local machine. If something goes wrong with Moltbot, the damage can spread across every service you connected. Email, calendar, messaging apps, financial accounts, and anything else you gave it access to becomes vulnerable.
Herk's conclusion: Claude Code wins on security and proven results. Moltbot wins on accessibility and the feeling of having a true AI assistant. But Steinberger himself warned that "most non-techies should not install this."
The Case Against Moltbot: Why Some Say It Is Mostly Hype
One YouTuber tested Moltbot extensively and reached a harsh conclusion. He argues that Moltbot is essentially Opus 4.5 wrapped around Telegram with scheduling capabilities. The ability to send scheduled messages and work from your phone is useful but not new. People have been doing similar things with automation tools for months.
He traced part of the viral spread to the crypto pump-and-dump scheme. Scammers used hijacked accounts to create artificial buzz around the fake token. Some of the social media hype was driven by people trying to inflate token prices, not genuine enthusiasm for the technology.
The use cases he observed were often unimpressive when examined closely. Organizing files by type, summarizing chat messages, and doing "market research" are tasks that feel productive but often produce nothing of real value.
His main criticisms:
- The tool chews through tokens fast. One user spent $300 in two days on what they considered basic tasks.
- Many viral demos showed functionality that already exists in simpler tools.
- The project is only three months old. Nobody has proven long-term ROI or revenue generation.
- The hype cycle attracted grifters selling courses and sponsorships more than genuine users.
His final take: Moltbot(Openclaw) does not help you make money. It represents an incremental step toward decentralized AI agents, not a breakthrough product. The technology is interesting for experimentation but not ready for serious business use.
Security Risks: Why Experts Are Warning Against Openclaw
The security problems with Openclaw go beyond typical software bugs. The tool's core design creates risks that many users do not understand when they install it.
The Exposed Server Problem
Security researchers scanned the internet for Moltbot(Openclaw) installations. They found many instances exposed to the public web with weak or missing authentication. Using a tool called Shodan, they could search for "Clawdbot Control" and find complete credentials.
What they found on exposed servers:
- Full API keys for AI services
- Bot tokens for messaging platforms
- OAuth secrets for connected accounts
- Complete conversation histories from private chats
- The ability to send messages as users
- Command execution capabilities
According to The Register, of the servers examined manually, eight had zero authentication. Anyone could access them, run commands, and view all configuration data. Forty-seven had working authentication that researchers confirmed was secure. The rest fell somewhere in between with partial protection.
The Prompt Injection Risk
Openclaw reads content from many sources: emails, documents, web pages, messages. Any of these can contain hidden instructions that trick the AI into taking harmful actions.
In one demonstration documented on Medium, a researcher sent a malicious email to a Openclaw instance. The email contained hidden text instructing the bot to forward the user's last five emails to an attacker's address. The AI read the email, believed the instructions were legitimate, and executed them. The entire attack took five minutes.
This is not a theoretical risk. Every document, email, and webpage that Openclaw reads becomes a potential attack point. The tool ships without guardrails by default, which is a design choice that prioritizes power over safety.
What Security Experts Are Saying
Google VP Heather Adkins: "My threat model is not your threat model, but it should be. Don't run Clawdbot."
Cisco: "From a capability perspective, Moltbot is groundbreaking. This is everything personal AI assistant developers have always wanted to achieve. From a security perspective, it's an absolute nightmare."
Hudson Rock: "ClawdBot represents the future of personal AI, but its security posture relies on an outdated model of endpoint trust. Without encryption-at-rest or containerization, the 'Local-First' AI revolution risks becoming a goldmine for the global cybercrime economy."
Salt Security (via The Register): "A significant gap exists between the consumer enthusiasm for Clawdbot's one-click appeal and the technical expertise needed to operate a secure agentic gateway. While installing it may resemble a typical Mac app, proper configuration requires a thorough understanding of API posture governance to prevent credential exposure due to misconfigurations or weak authentication.
Many users unintentionally create a large visibility void by failing to track which corporate and personal tokens they've shared with the system. Without enterprise-level insight into these hidden connections, even a small mistake in a 'prosumer' setup can turn a useful tool into an open back door, risking exposure of both home and work data to attackers."
The Supply Chain Attack
Jamieson O'Reilly, founder of red-teaming company Dvuln, uploaded a skill to ClawdHub, the tool's plugin library. He artificially inflated the download count to more than 4,000. Developers from seven countries downloaded the poisoned package.
The skill he uploaded was harmless, but it proved he could have executed commands on any Openclaw instance that installed it. The payload contacted his server to confirm execution occurred. He could have stolen credentials, exfiltrated code, or turned Openclaw into a backdoor.
SOC Prime's analysis noted: "A proof-of-concept supply-chain attack uploaded a malicious skill to the ClawdHub library, demonstrating remote command execution for downstream users."
Credentials in Plain Text

Openclaw stores secrets in Markdown and JSON files without encryption. API keys, tokens, and passwords sit in readable text files on the host machine. Hudson Rock warned that common malware like RedLine, Lumma, and Vidar can easily grab these files.
If any malware gets onto a machine running Openclaw, every credential the bot has access to becomes compromised. This includes all the services you connected: email, calendar, messaging apps, and anything else.
How to Secure Openclaw If You Still Want to Use It
If you understand the risks and want to proceed anyway, security hardening is essential. The image below shows the top ten vulnerabilities and their fixes.

Critical Security Fixes:
Vulnerability | How to Fix It |
|---|---|
Gateway exposed on 0.0.0.0:18789 | Set gateway.auth.token in your environment variables |
DM policy allows all users | Change dm_policy to allowlist with specific usernames only |
Sandbox disabled by default | Enable sandbox=all and set docker.network=none |
Credentials stored in plaintext oauth.json | Move credentials to environment variables, set chmod 600 permissions |
Prompt injection through web content | Wrap all untrusted content in untrusted tags |
Dangerous commands unblocked | Block rm -rf, curl pipes, and git push --force |
No network isolation | Use Docker network isolation |
Elevated tool access granted | Restrict MCP tools to the minimum set you actually need |
No audit logging | Enable comprehensive session logging |
Weak or default pairing codes | Use cryptographic random codes with rate limiting |
These fixes require technical knowledge. You need to understand environment variables, file permissions, Docker networking, and security best practices. If these terms are unfamiliar, you should not be running Openclaw.
Steinberger himself said: "Most non-techies should not install this. It's not finished. I know about the sharp edges. It's only 3 months old."
Who Should Not Use Openclaw
Openclaw is not ready for mainstream users. The tool requires technical expertise that most people do not have. Even experienced developers report spending hours debugging configuration issues.
You should avoid Openclaw if:
- You do not understand servers, permissions, or virtual machines
- You plan to run it on your primary laptop with your passwords and bank information
- You expect a plug-and-play experience similar to ChatGPT
- You handle sensitive data for work or personal finance
- You cannot monitor and sandbox the tool properly
- You are not comfortable reading security advisories and applying fixes
Openclaw might work for you if:
- You are a technical founder or indie hacker who understands security concepts
- You are a developer comfortable running servers and configuring APIs
- You want to experiment with the future of autonomous AI agents
- You have a dedicated machine or VPS separate from your main computer
- You can accept that things will break and require debugging
- You understand that your data could be exposed if you make configuration mistakes
The project will likely improve over time. More security features will be added. Documentation will get better. But right now, the tool rewards patient, careful, and technically skilled users. Everyone else should wait.
Elephas: A Safer Alternative for AI Assistance
While Openclaw grabs headlines with viral demos and security warnings, other tools offer AI capabilities without the same risks. Elephas is a Mac-native AI assistant that keeps your data private and works completely offline.
The core difference is architecture. Openclaw runs on servers that can be exposed to the internet. Elephas can run entirely on your Mac with inbuilt local LLM models. Your data never leaves your device unless you choose to use cloud AI models.
How Elephas Compares to Openclaw:
Feature | Openclaw | Elephas |
|---|---|---|
Data Storage | Servers (often exposed), plaintext files | All data stays on your Mac |
Offline Mode | Requires internet for most AI models | True offline with built-in local AI |
Security | 900+ servers found exposed, prompt injection risks | No servers, no internet exposure |
Setup | Needs VPS or dedicated hardware, technical configuration | Install on Mac and start using |
Platform | Multi-platform but complex setup | Native Mac, iPhone, iPad |
Internet Required | Yes for most functionality | No, works fully offline |
Elephas includes features that address similar needs without the security concerns:
- Super Brain lets you build a personal knowledge base from your documents, notes, and web content. You can ask questions about your own files and get answers based on your personal data.
- Multiple AI Options give you flexibility. Use the built-in local models for complete privacy. Or connect your own API keys for ChatGPT, Claude, Gemini, Grok, or Perplexity when you want cloud model capabilities.
- Integrations connect to Apple Notes, Obsidian, Notion, LogSeq, Roam Research, and DEVONthink. Your existing workflows stay intact.
- Workflow Automation with AI agents handles multi-step tasks. You can create automated processes for repetitive work.
- Web Search is built in for research tasks that need current information.
The pricing model differs too. Elephas is a one-time purchase or you can get it for $9.99/month. Openclaw is free but requires ongoing API costs that can spike unpredictably.
Openclaw gives you more raw power at the cost of security and complexity. Elephas gives you solid AI capabilities without exposing your data to the internet or requiring a dedicated server.
Final Take
Openclaw represents a real glimpse of where personal AI assistants are heading. The concept of an always-on AI that manages your digital life, takes action on your behalf, and learns your preferences over time is genuinely exciting. The viral demos showed things that felt like science fiction just a year ago.
But the execution is not ready for mainstream use.
Over 900 servers were found exposed with no authentication. Prompt injection attacks can steal your data in minutes. Crypto scammers exploited the hype to steal millions. Malware disguised as Openclaw extensions infected Windows machines. The creator himself warns non-technical users to stay away.
The tool works best for developers, security-conscious power users, and people willing to experiment on isolated machines. It rewards patience, technical skill, and careful configuration. Everyone else should wait until the sharp edges get smoothed out.
For most people who want AI assistance today, safer alternatives exist. Tools like Elephas offer similar capabilities for knowledge management, writing assistance, and workflow automation. They work offline, keep your data on your device, and do not require you to run a server or manage security configurations.
The future of AI assistants is coming. Openclaw shows us what that future might look like. But for now, the present version carries risks that outweigh the benefits for the average user.
Comments
Your comment has been submitted